Enterprise Wireless Airspace Defense
Gain complete visibility into your RF spectrum with advanced wireless intrusion detection that safeguards your organization from unauthorized devices, rogue access points, and sophisticated wireless threats.
100%
Passive RF Detection
1-3m
Device Location Accuracy
50+
RF Protocols Monitored
24/7
Real-time Protection
Comprehensive Wireless Security Features
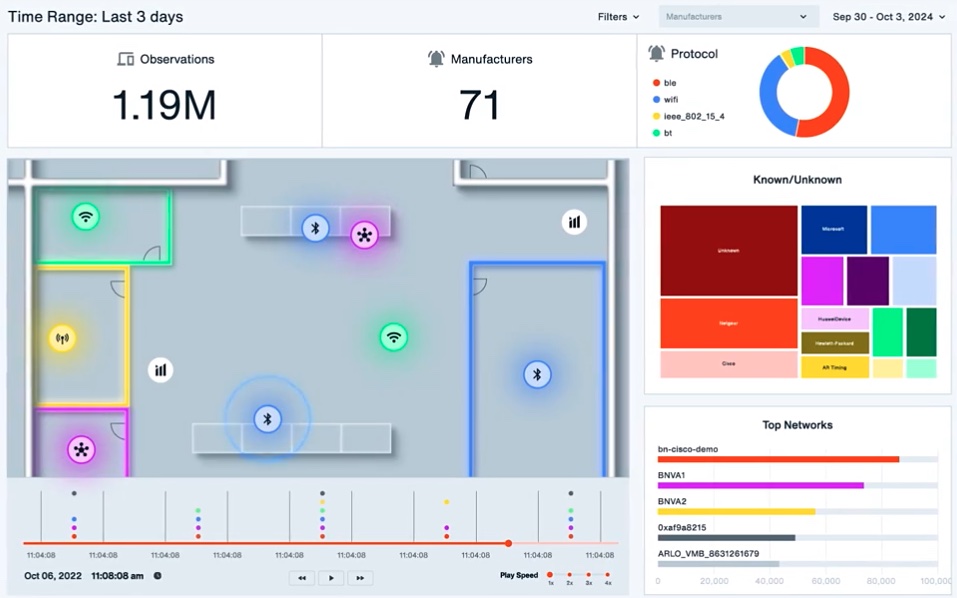
Full-Spectrum RF Monitoring
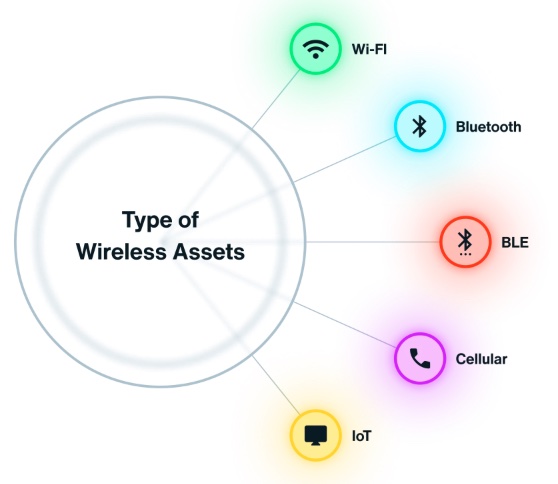
Monitor and analyze the complete radio frequency spectrum, detecting cellular, Bluetooth, Wi-Fi, and IoT devices across all wireless protocols for total visibility into your airspace.
Advanced Threat Detection
Identify and classify unauthorized devices, rogue access points, eavesdropping attempts, and sophisticated wireless attacks using machine learning and proprietary RF fingerprinting.
Precise Device Localization
Accurately locate any wireless device within 1-3 meters, enabling rapid response to security threats and real-time tracking of unauthorized transmitters within your facility.
Wireless Threats We Detect
Unauthorized Mobile Devices
Detect smartphones, tablets, and other cellular devices operating within restricted areas, even when Wi-Fi and Bluetooth are disabled, preventing data exfiltration and espionage.
Rogue Access Points
Identify unauthorized Wi-Fi networks, evil twins, and malicious hotspots designed to intercept network traffic, conduct man-in-the-middle attacks, or create backdoors into your network.
Bluetooth Exploits
Detect Bluetooth and BLE-based attack tools like MouseJack, KeySniffer, and Flipper Zero that can be used to compromise keyboards, mice, and other wireless peripherals or exfiltrate data.
Surveillance Devices
Locate hidden wireless cameras, microphones, RFID tracking tags, and other covert surveillance equipment that could compromise executive privacy or intellectual property.
Protect Critical Environments
Secure Facilities
Protect classified areas, SCIFs, board rooms, and R&D labs from unauthorized wireless devices, eavesdropping equipment, and covert data exfiltration attempts.
Cloud & Data Centers
Ensure the integrity of cloud infrastructure by detecting unauthorized wireless devices, rogue networks, and RF-based attacks that could threaten customer data and system availability.
Critical Infrastructure
Safeguard industrial control systems, SCADA networks, and IoT devices from wireless attacks that could disrupt operations or create security vulnerabilities in critical systems.
How Our Technology Works
Passive RF Monitoring
Software-defined radio technology continuously scans the full RF spectrum to detect all wireless emissions within your environment, without disrupting legitimate network traffic.
RF Fingerprinting & Classification
Advanced machine learning algorithms analyze signal characteristics to identify device types, protocols, and potential threats, even detecting devices attempting to hide their presence.
Precision Localization
Triangulation technology pinpoints the physical location of any wireless device within 1-3 meters, enabling security teams to quickly find and address unauthorized equipment.
Real-time Alerting & Response
Automatic alerts notify security teams of potential threats, with integrated remediation options and detailed forensic data to support incident response.
Beyond Traditional Wireless Security
| Capabilities | Our WIDS Platform | Traditional Solutions |
|---|---|---|
| Cellular Detection | ✓ Even with Wi-Fi/Bluetooth off | Limited or not available |
| Protocol Coverage | ✓ 50+ wireless protocols | Wi-Fi and Bluetooth only |
| Location Accuracy | ✓ 1-3 meter precision | Zone-level or not available |
| Forensic Capabilities | ✓ Historical movement tracking | Limited event logs only |
| Integration | ✓ SIEM, SOAR, XDR compatible | Limited integration options |
Frequently Asked Questions
How is this different from my existing network security?
Traditional network security focuses on protecting data once it's on your network. Our wireless airspace defense platform operates at the RF level (layers 0-2), detecting threats before they can connect to your network and monitoring all wireless signals, not just Wi-Fi, providing protection against the full spectrum of wireless threats.
Does this system interfere with legitimate wireless usage?
No, our system is 100% passive, only monitoring the RF spectrum without emitting any signals. This means it won't interfere with legitimate wireless communications, medical devices, or other sensitive equipment while still providing comprehensive security monitoring.
How quickly can the system be deployed?
Our enterprise solution can be fully deployed within 2-4 weeks for most facilities. We also offer rapid deployment kits for temporary installations that can be operational within hours, ideal for events, executive meetings, or emergency response scenarios.
Secure Your Wireless Airspace Today
Protect your organization from the growing threat of wireless attacks with our comprehensive RF security solution.